Is IoT Security Finally Getting the Attention of Tech Giants?
Is IoT Security Finally Getting the Attention of Tech Giants?
- Last Updated: December 2, 2024
Yitaek Hwang
- Last Updated: December 2, 2024



Recently, Google and Microchip announced an interesting partnership to improve security in IoT devices by establishing both hardware and software root of trust. In light of recent, growing IoT based attacks (Mirai, WannaCry, BlueBorn, Krack), IoT security is finally getting the attention of tech giants.
We’ve grown accustomed to blockchain being kicked around as a potential solution, but have not seen actual implementations of blockchain used for mass IoT deployments just yet. So, what makes this announcement by Google and Microchip special? We’ll summarize the presentation by Antony Passemard (Google Cloud IoT Product Management Lead) and Nicolas Schieli (Sr. Strategic Marketing Manager at Microchip).
Root of Trust & Device Identity
One critical component in IoT is device identity. The system must be able to verify the identity of the device to trust its data and to access the broader system. In order to establish a root of trust, device identity should be unique, verifiable, and trustable, as well as being able to validate device firmware.
In practice, device identity is often established with cryptographic key pairs: one private key and one public key, related by a mathematical algorithm. The private key must remain secret for the entire lifetime of the product or a malicious player might use that private key to act as the hijacked device. To accomplish this, the private key must be isolated from users, software, and microcontrollers. The private key must also be protected against manipulation during the manufacturing phase.
Hardware Root of Trust
Microchip’s CryptoAuthentication device achieves this by storing the cryptographic engine and other algorithm generators (monotonic counters, random number generator) inside tamper-hardened hardware that gets embedded as a companion to any microcontroller or processor. This means that keys are generated by the device and completely isolated by the rest of the board/software. So when the identity of the device needs to be verified, the microcontroller sends a message to the crypto hardware, which combines it with the private key to generate a hashed response.
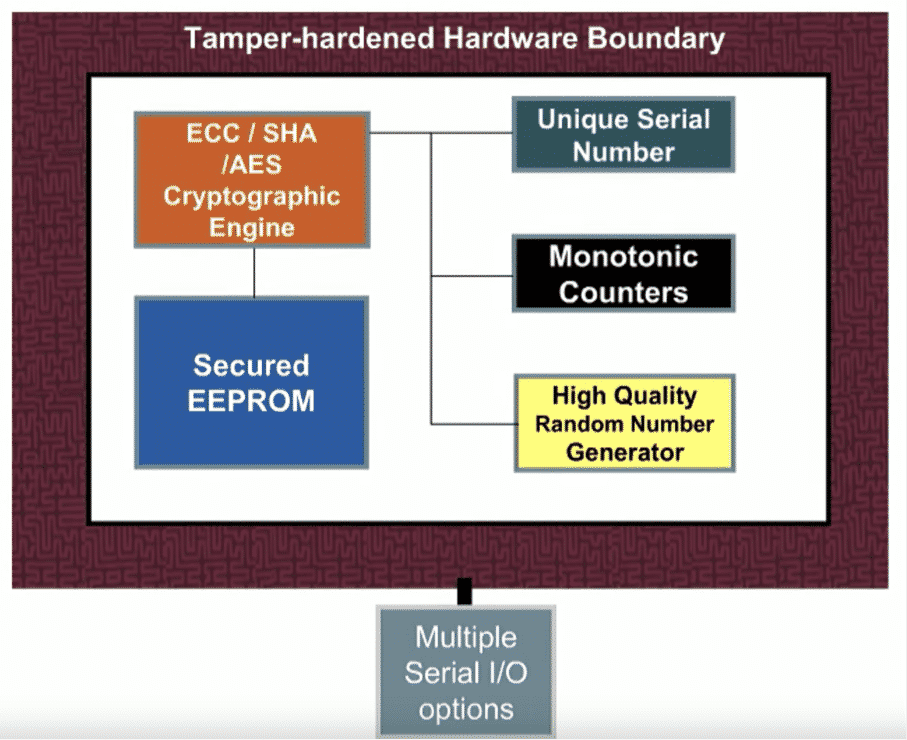
Integration with Cloud IoT Core
In a previous article, we introduced Cloud IoT Core and how it simplifies secure device management. But to quickly recap, devices can establish a TLS session to Google, connect via MQTT or HTTP using a JWT signed by the private key as its password, and IoT Core will validate the device by inspecting the JWT with the device public key.
The big takeaway here is that the device is responsible for only securely managing the private key. It doesn’t need the heavy TLS stack, so crypto hardware can be smaller and focus on one thing. This is where Microchip’s CryptoAuthentication device works nicely with Cloud IoT Core.
To borrow from the presentation, a typical flow without a crypto device looks like this: (Note: Device Manager and MQTT/HTTP brokers are part of Cloud IoT Core)
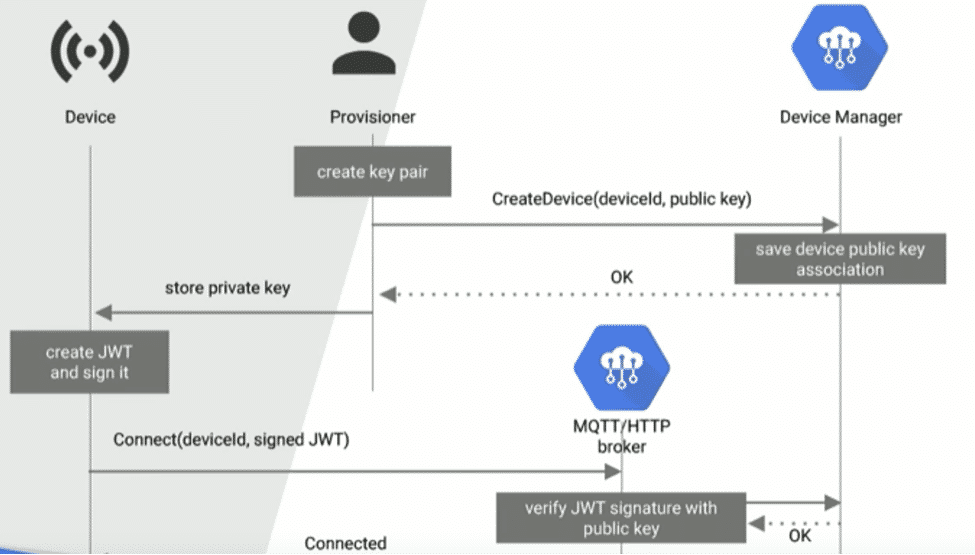
The provisioner must create the key pair, and then pass on the private key and burn it onto the device. This is not a secure practice because now the device has access to this private key directly.
Compare that to the secure flow with Microchip. Now the key is generated by the device itself, and the public keys are passed to the provisioner, who can then use that to interface with IoT Core.
<!-- wp:paragraph --> <p>This significantly reduces the risk of leaking the private keys in the certificate chain process and, by the virtue of Google taking care of the TLS stack, allows the chip itself to be lightweight and easily integrated into other boards.</p> <!-- /wp:paragraph -->
<!-- wp:heading --> <h2 class=" />The Big Picture
For any player involved in the IoT landscape, security configuration is a pain. The partnership between Microchip and Google starts to simplify that process and begins to provide security as a service.
With a chip that has a small footprint and a secure, Google-managed service that is backed by its massive infrastructure, one can start to add security to their IoT systems smoothly. This is by no means a perfect solution. If you can’t use MQTT/HTTP, you can’t use IoT Core and your board space might be extremely limited to add on Microchip’s device. But this move by industry giants suggests a positive outlook on device security.
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

What is Software-Defined Connectivity?
Related Articles



