IoT Security Must-Haves
IoT Security Must-Haves
- Last Updated: December 2, 2024
SpinDance
- Last Updated: December 2, 2024



The growth of the Internet of Things (IoT) products and services continues to boom. It’s become an expectation that most things are connected and taking advantage of cloud-based digital services. There are, of course, important security implications for all these connected devices. We’ve all heard of examples of IoT hacking. What makes matters worse is that the more successful your product is, the more attention you attract from would-be attackers. This article is Part 1 of a series about IoT security must-haves and best practices for all IoT products.
'IoT security is on track to continue to evolve and improve. Every year it gets a bit easier and cheaper for product makers to implement security features.' - SpinDance
The revenue impact of an attack on your IoT systems can be significant. Some reports indicate that companies have lost up to 25 percent of their revenue following a cyber attack. Additionally, the estimated cost to an organization of an attack on one of their IoT devices is $330,000. This is a painful proposition for most business leaders. Yet, the business value that IoT products and services provide remains strong and they continue to be launched in large numbers.
Fortunately, the industry has made massive strides over the last several years to make IoT devices more secure and more difficult to attack. IoT security is on track to continue to evolve and improve. Every year it gets a bit easier and cheaper for product makers to implement security features.
The following list is the top security must-haves for all IoT products. If you don’t have these must-haves in your product, then you could be overly vulnerable to attack.
A Little About Cryptography
If you will be involved in an IoT product or service initiative, we highly recommend you get familiar with cryptography. Cryptography plays an important part in nearly all aspects of IoT security. There are several great online courses available to learn the basics. Your level of required knowledge depends on your role in your organization. For developers, we recommend a very strong set of knowledge and experience with security for IoT.
Some important terminology:
- Cryptography - The transformation of data in order to hide its true content. Also used to verify integrity and authentication.
- Cryptographic Key - A numerical value that is used in cryptographic operations. The larger the key, the stronger the cryptography.
- Symmetric cryptography - The same key that is used to encrypt data is used to decrypt it. Thus the key needs to be shared between parties. Due to its relative efficiency, it is still used today for the bulk of communications.
- Asymmetric cryptography - A different key is used to encrypt the data versus the key to decrypt it. The two keys form a private and public key pair. The private key must never be shared. This type of encryption is critical to authentication.
- Certificate - A set of data that uniquely identifies an entity including its public key and other information. The certificate is digitally signed to prove its authenticity (see below).
- Hash - An algorithm that maps strings of bits (like the data of a certificate) to fixed-length strings of bits. It’s a much shorter unique value that is calculated from a much larger set of data. Any small change to the input data causes a drastic change to the hash.
- Digital Signature - The result of a cryptographic transformation of data (such as a hash) that, when properly implemented, proves origin authentication and data integrity. Usually, you take the public key from the certificate authority that signed the certificate, decrypt the signature, and compare it to the hash you calculated from the certificate data. If it matches, it is good.
- Certificate Authority - A trusted entity that issues and revokes certificates. They sign certificates.
The effectiveness of cryptography depends on the computational infeasibility of brute force attacks - which means that it would take too much time for an attacker to exhaustively try every conceivable key in order to find the right key to unlock your data.
Must-Have # 1: Secure Identity
What is it?
Devices and cloud services in an IoT system need to trust each other. This trust becomes the foundation for all their interactions. Secure identity is unique and unclonable proof that the device or service is who it says it is. Each device or service uses a unique verifiable identity in the form of a certificate to gain access to other parts of the system it is authorized to access.
How does it work?
A device’s identity is encapsulated into a unique certificate and a private key. The certificate is signed by a trusted certificate authority. This certificate contains identifying details about the device such as its unique name and serial number. It also contains the device’s public key, associated with its private key that is kept secret and never shared. When connecting to a cloud service, the device provides its identity certificate. The service verifies its authenticity by checking the certificate’s signature. Most IoT systems use the x509 certificate format which is the same format used to manage the identity of secure websites.
Many embedded systems offer specific features for generating and securely storing identity certificates. These are often part of systems called a Root-of-Trust. Additionally, cloud service providers offer tools and infrastructure to get device certificates signed and injected into the devices. This is typically called provisioning. For example, AWS provides infrastructure for provisioning devices with the provisioning features of AWS IoT Core.
Why is it important?
With a unique, verifiable, and unclonable identity for every valid device, IoT systems have more assurances that unauthorized clones or invalid interactions cannot happen.
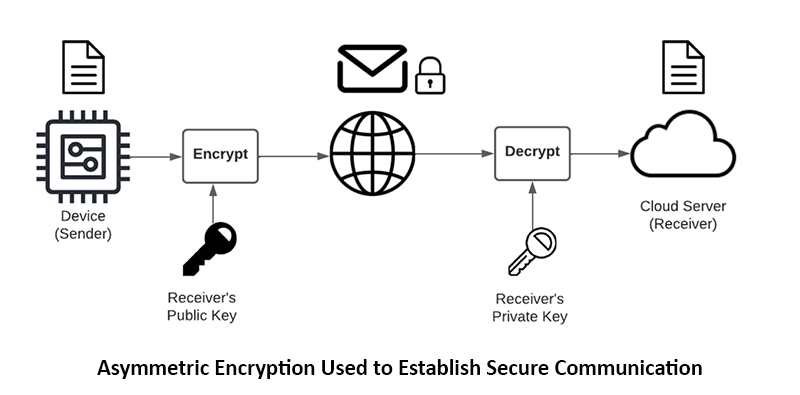
Must-Have # 2: Secure Communication
What is it?
IoT devices need to communicate on the internet securely. Secure communication usually refers to these three pillars.
- Privacy - preventing potential eavesdroppers from being able to interpret sent and received messages
- Integrity - preventing an attacker from tampering with messages and passing them off as valid
- Authentication - Ensuring both the sender and the receiver of messages are who they say they are
How does it work?
Since communication on the internet flows through public infrastructure, anyone can view data that is communicated between endpoints. With encryption, the data is obscured and mathematically infeasible to decode without the key. Only the sender and the receiver should be able to understand the data. Eavesdroppers should not be able to understand anything from the data, it should effectively be opaque.
To thwart would-be imposters from trying to establish communications with your systems (a man-in-the-middle attack), each party needs to be able to mutually authenticate the other. This is accomplished through identity certificate signature verification. Only a valid endpoint with a valid certificate that was signed by a mutually trusted certificate authority will pass the verification test.
Most IoT systems use Transport Layer Security (TLS) which provides the backbone of secure websites. As an example, a popular operating system for IoT devices, AWS FreeRTOS, includes a secure sockets library based on a popular open-source TLS library, mbedTLS from Arm.
Why is it important?
A system that ensures privacy, integrity, and authentication in its communications will have more protection against unauthorized activities such as eavesdropping, tampering, system hijacking, or denial of service.
Source: SpinDance
Must-Have # 3: Secure Storage
What is it?
IoT systems need to keep sensitive information secret and protected. They need confidentiality.
Secure storage refers to various techniques to secure data and protect it from unauthorized access. It also means encrypting data such that if an intruder did get access, they wouldn’t be able to make sense of it. This includes data stored on devices as well as in the cloud. It also includes hiding away cryptographic keys in lockboxes that aren’t accessible by anything other than the cryptographic engines that require them.
How does it work?
Many embedded systems offer low-level support for secure storage including flash protection, encrypted code storage, encrypted file systems, and data integrity monitoring. An example includes Espressif ESP32 flash encryption. Cloud providers offer encrypted object storage, encrypted databases, and key management services. Access is controlled through security policies linked to user authentication. Examples include the encryption options available with AWS S3 object storage and AWS RDS, utilizing keys stored in AWS Key Management Service or AWS Secrets Manager.
Why is it important?
Keeping data safe is of critical importance for many reasons. IoT systems store sensitive data including intellectual property, network, and other security credentials, customer data, and more. Implementing secure storage techniques will help prevent potential attackers from doing things like reverse engineering code, injecting malware, cloning devices illegally, impersonating devices, and breaching customer data.

Source: SpinDance
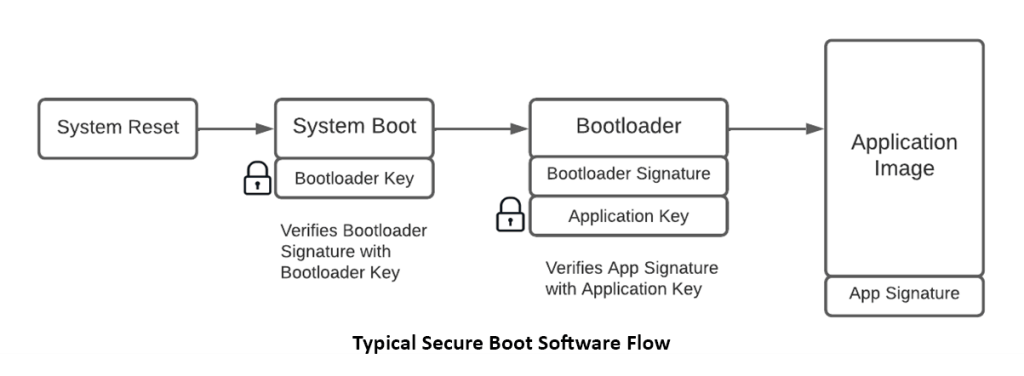
Must-Have # 4: Secure Boot
What is it?
Secure boot or sometimes called Trusted boot or by other names, is a process by which the characteristics of the software to run on the device (aka boot up ) are checked against known-good quantities to verify their integrity and trustworthiness. This all happens before the system attempts to run the software.
How does it work?
It works similarly to how certificates are signed and verified. A hash is calculated from the data to be loaded into the device’s flash memory (the code). This hash is unique and any unauthorized changes to the code in the flash will cause the hash to veer wildly off. The hash is then cryptographically signed by a trusted party, and the trusted party’s public key is stored securely in the device. When the device powers up, it checks the integrity and authenticity of the code by decrypting the signature and comparing it to the hash it independently calculated from its flash memory. If it matches, it is okay to run the code. If not, a potentially unauthorized modification may have happened and the device instead goes into a safe mode. Secure boot is usually accomplished in stages. Each stage is signed and verified independently. A small program called a bootloader does most of the work.
The Espressif ESP32, supports secure boot, as do several other microcontrollers targeted for IoT applications, such as Nordic nRF52840, Infineon PSoC 64, and NXP LPC55S69.
Why is it important?
Securing the boot process provides added protection against malware attacks. If an attacker is able to bypass other security features and add their own sinister modifications to the system firmware, the secure boot algorithm will stop it in its tracks.
Source: SpinDance
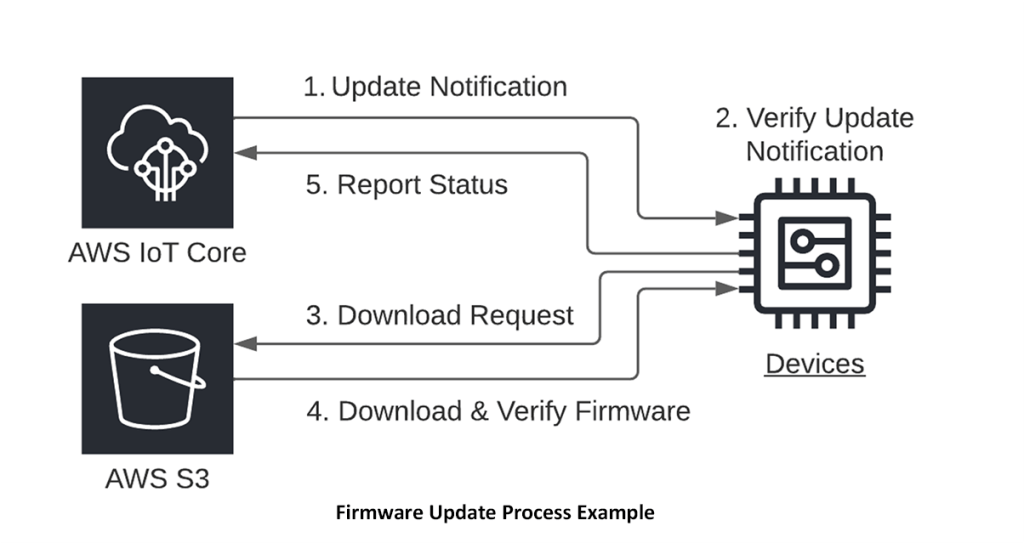
Must-Have #5: Secure Over-The-Air Firmware Updates
What is it?
Secure Update, often called Over-The-Air (OTA) or Firmware update Other The Air (FOTA), etc is the process of updating the firmware on devices remotely, which is typically done over wireless communication. Effectively doing this requires each foundational security feature that we’ve already discussed plus additional infrastructure and logic.
How does it work?
When devices are provisioned in a factory, they receive security credentials and get registered with the update service such that they are authorized to receive updates. The credentials and the registration must be tied to its unique device identity. If a problem is detected with a device later on (such as if it has been compromised by an attacker), its registration can be revoked.
The firmware to be deployed is cryptographically signed. The devices get notified when there is an update available. This notification message includes the location of the update file to download. At an appropriate time, the device downloads the update, verifies it, and loads it in its flash memory. Then the device resets and the secure boot takes over to verify and boot up the new software. Often devices store a backup copy of their firmware in case anything goes wrong in the update process. However, it is important to detect when a device is running old firmware and limit what it can do to avoid roll-back attacks where attackers intentionally roll back the firmware to an older version with a known vulnerability.
As an example, AWS supports Secure Updates with the AWS FreeRTOS OTA Update Manager service and AWS IoT Jobs.
Why is it important?
With secure updates, you have the ability to respond quickly to emerging security issues and patch software on devices that are already in the hands of customers. With secure updates, not only can you patch problems, but you can also make improvements and enhancements to continually delight your customers.
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

Moving Past the Pilot Phase in IoT and AI
Related Articles