Sopris: Microsoft’s Solution to IoT Security Problems
Sopris: Microsoft’s Solution to IoT Security Problems
- Last Updated: December 2, 2024
Yitaek Hwang
- Last Updated: December 2, 2024



MIT Technology Review recently named “Botnets of Things” as one of the top 10 breakthrough technologies in 2017. From internet-connected kiosks to medical devices, IoT security problems have been stealing the headlines since the infamous Mirai attack last year.
We previously covered Google’s Infrastructure Security Design and CryptoNets as software approaches to security. This week, we dive into the “Seven Properties of Highly Secure Devices” by Microsoft Research NExT Operating Systems Technologies Group to see how we can bring security to the microcontroller level to complete the IoT stack.
Fixing IoT Security Problems
The goal of the research was to identify and implement security protocols for the billions of smart devices powered by microcontrollers. Despite the complete lack of security properties in current devices, the researchers remain bullish that IoT security problems can be addressed at the hardware level regardless of the price. Mainly, the purpose of this paper is two-fold: 1) establishing 7 properties required to achieve high security, 2) demonstrating the feasibility with a prototype.
7 Properties of Highly Secure Devices
According to the Microsoft research group, the minimum requirements to secure connected devices are the following:
- Hardware-based Root of Trust: physical countermeasures built-in to resist side-channel attacks (e.g. pulse testing the reset pin to prevent glitching attacks).
- Small Trusted Computing Base: private keys stored in a secure vault, separated from the software.
- Defense in Depth: multiple layers & checkpoints for defense.
- Compartmentalization: hardware-enforced barriers to prevent failure in one area to affect others.
- Certificate-based Authentication: signed certificates, not passwords, used to establish identities.
- Renewable Security: periodic updates to the software to keep security state up to date.
- Failure Reporting: compiling reported failures to build up a better response routine.
To our astute reader, many of these principles seem obvious. However, the real contribution by the Microsoft team lies in demonstrating the feasibility of implementing all seven principles in low-cost microcontrollers.
Sopris: Modified MT7687
The team at Microsoft took a low-power smart home chipset MT7687 from MediaTek Labs to build in multiple levels of security. Figure 1 below shows the architecture of the MT7687 device. While it already contains cryptographic engines to provide some level of security, it fails to provide sufficient security due to its lack of compartmentalization and defense in depth.
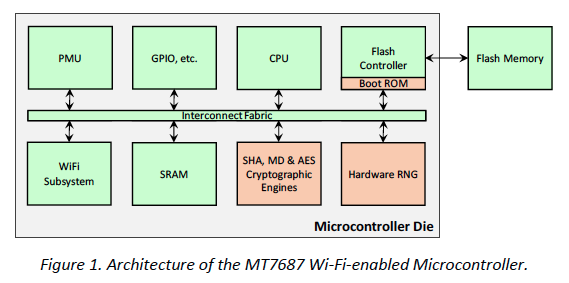
Image credit: Microsoft
Compare the previous design with the modified design shown below. The new design has multiple levels of isolation and process-isolated compartments inside what Microsoft named the Pluton Security Subsystem.
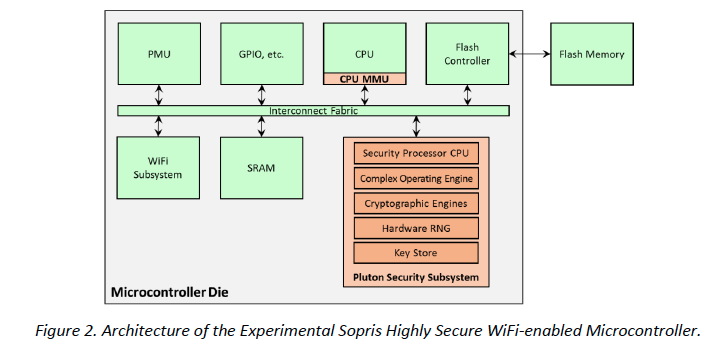
Image credit: Microsoft
While the paper doesn’t report the added cost to implement Pluton, the researchers state that the next phase will detail packaging Pluton into a simple device board for mass production. Although demonstrating feasibility on a single existing board doesn’t prove that security solved, Microsoft is leading the discussion to push security design considerations to the hardware level.
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

How Drones and Telecom Enable Aerial IoT
Related Articles


